Advertisements
Kevin Mitnick Quotes
Advertisements
Advertisements
Advertisements
Advertisements
 Friendship Quotes
Friendship Quotes
 Love Quotes
Love Quotes
 Life Quotes
Life Quotes
 Funny Quotes
Funny Quotes
 Motivational Quotes
Motivational Quotes
 Inspirational Quotes
Inspirational Quotes
Advertisements
Text Quotes
At the end of the day, my goal was to be the best hacker (Kevin Mitnick Quotes)
Social engineering bypasses all technologies, including firewalls (Kevin Mitnick Quotes)
To some people I’ll always be the bad guy (Kevin Mitnick Quotes)
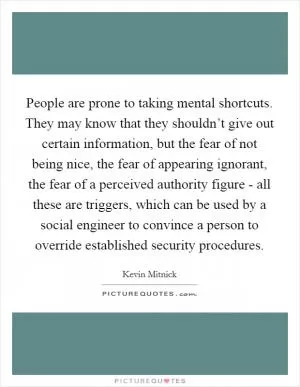
People are prone to taking mental shortcuts. They may know that they shouldn’t give out certain information, but the fear of not being nice, the fear of appearing ignorant, the fear of a perceived authority figure - all these are triggers, which can be used by a social engineer to convince a person to override established security procedures. (Kevin Mitnick Quotes)
I get hired to hack into computers now and sometimes it’s actually easier than it was years ago. (Kevin Mitnick Quotes)
Somebody could send you an office document or a PDF file, and as soon as you open it, it’s a booby trap and the hacker has complete control of your computer. Another major problem is password management. People use the same password on multiple sites, so when the hacker compromises one site, they have your password for everywhere else. (Kevin Mitnick Quotes)
My hacking involved pretty much exploring computer systems and obtaining access to the source code of telecommunication systems and computer operating systems, because my goal was to learn all I can about security vulnerabilities within these systems. (Kevin Mitnick Quotes)
I’m still a hacker. I get paid for it now. I never received any monetary gain from the hacking I did before. The main difference in what I do now compared to what I did then is that I now do it with authorization. (Kevin Mitnick Quotes)
I get hired by companies to hack into their systems and break into their physical facilities to find security holes. Our success rate is 100%; we’ve always found a hole. (Kevin Mitnick Quotes)
Phone phreaking is a type of hacking that allows you to explore the telephone network by exploiting the phone systems and phone company employees. (Kevin Mitnick Quotes)
Security is always going to be a cat and mouse game because there’ll be people out there that are hunting for the zero day award, you have people that don’t have configuration management, don’t have vulnerability management, don’t have patch management. (Kevin Mitnick Quotes)
One of my all-time favorite pranks was gaining unauthorized access to the telephone switch and changing the class of service of a fellow phone phreak. When he’d attempt to make a call from home, he’d get a message telling him to deposit a dime, because the telephone company switch received input that indicated he was calling from a pay phone. (Kevin Mitnick Quotes)
Businesses should absolutely set aside funding in their budgets for security consultants. Unless there is an expert on staff, and there usually is not, it needs to be outsourced. (Kevin Mitnick Quotes)
What happens with smaller businesses is that they give in to the misconception that their site is secure because the system administrator deployed standard security products - firewalls, intrusion detection systems, or stronger authentication devices such as time-based tokens or biometric smart cards. But those things can be exploited. (Kevin Mitnick Quotes)
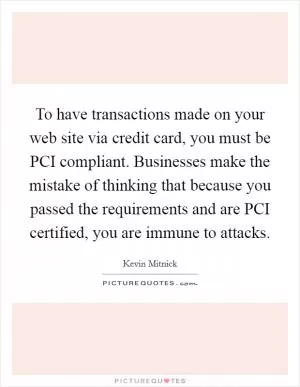
To have transactions made on your web site via credit card, you must be PCI compliant. Businesses make the mistake of thinking that because you passed the requirements and are PCI certified, you are immune to attacks. (Kevin Mitnick Quotes)
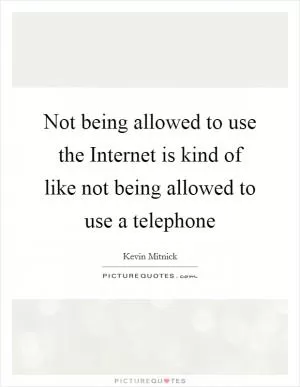
Not being allowed to use the Internet is kind of like not being allowed to use a telephone (Kevin Mitnick Quotes)
I don’t know of any case that involves computer hacking where there were multiple defendants charged where there wasn’t an informant on the case. (Kevin Mitnick Quotes)
Sometimes I get a call from my bank, and the first thing they ask is, ‘Mr. Mitnick, may I get your account number?’ And I’ll say, ‘You called me! I’m not giving you my account number!’ (Kevin Mitnick Quotes)
I trust online banking. You know why? Because if somebody hacks into my account and defrauds my credit card company, or my online bank account, guess who takes the loss? The bank, not me. (Kevin Mitnick Quotes)
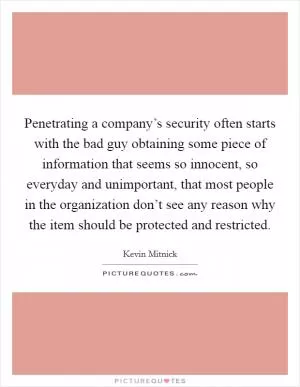
Penetrating a company’s security often starts with the bad guy obtaining some piece of information that seems so innocent, so everyday and unimportant, that most people in the organization don’t see any reason why the item should be protected and restricted. (Kevin Mitnick Quotes)
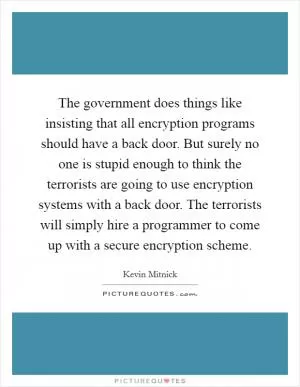
The government does things like insisting that all encryption programs should have a back door. But surely no one is stupid enough to think the terrorists are going to use encryption systems with a back door. The terrorists will simply hire a programmer to come up with a secure encryption scheme. (Kevin Mitnick Quotes)
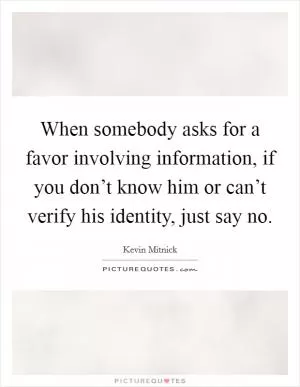
When somebody asks for a favor involving information, if you don’t know him or can’t verify his identity, just say no. (Kevin Mitnick Quotes)
Steve Wozniak and Steve Jobs founded Apple Inc, which set the computing world on its ear with the Macintosh in 1984. (Kevin Mitnick Quotes)
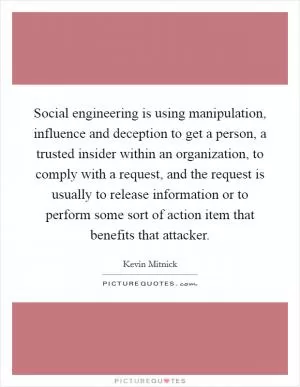
Social engineering is using manipulation, influence and deception to get a person, a trusted insider within an organization, to comply with a request, and the request is usually to release information or to perform some sort of action item that benefits that attacker (Kevin Mitnick Quotes)
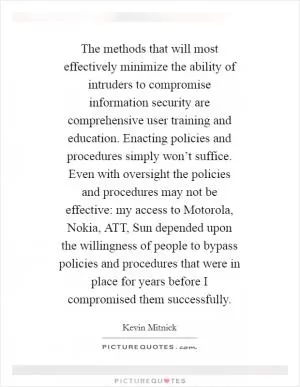
The methods that will most effectively minimize the ability of intruders to compromise information security are comprehensive user training and education. Enacting policies and procedures simply won’t suffice. Even with oversight the policies and procedures may not be effective: my access to Motorola, Nokia, ATT, Sun depended upon the willingness of people to bypass policies and procedures that were in place for years before I compromised them successfully (Kevin Mitnick Quotes)
Back up everything! You are not invulnerable. Catastrophic data loss can happen to you - one worm or Trojan is all it takes. (Kevin Mitnick Quotes)
I went from being a kid who loved to perform magic tricks to becoming the world’s most notorious hacker, feared by corporations and the government. (Kevin Mitnick Quotes)
I obtained confidential information in the same way government employees did, and I did it all without even touching a computer. ... I was so successful with this line of attack that I rarely had to go towards a technical attack. (Kevin Mitnick Quotes)
Nine out of every 10 large corporations and government agencies have been attacked by computer intruders. (Kevin Mitnick Quotes)
Protecting yourself is very challenging in the hostile environment of the Internet. Imagine a global environment where an unscrupulous person from the other side of the planet can probe your computer for weaknesses and exploit them to gain access to your most sensitive secrets. (Kevin Mitnick Quotes)